A new malware tool is being used by Chinese hacking group APT41 to monitor and save SMS traffic from specific phone numbers.
The tool, named MESSAGETAP, has been deployed in a telecoms network provider to support espionage efforts, according to a report from FireEye.
A statement from the security company said: “APT41’s operations have included state-sponsored cyber espionage missions as well as financially motivated intrusions. These operations have spanned from as early as 2012 to the present day.”
MESSAGETAP was discovered during a 2019 investigation at a telecoms network provider within a cluster of Linux servers responsible for routing and storing SMS message.
Image source: FireEye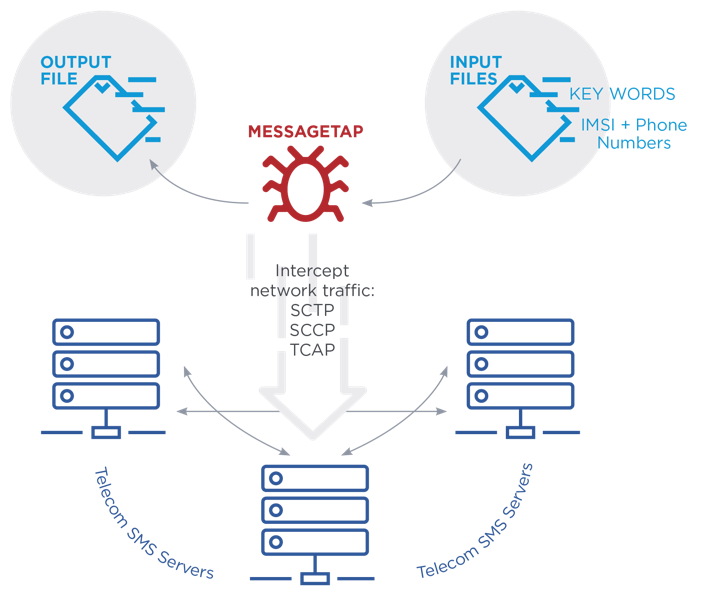
Evolving threats
FireEye said four unnamed telecoms organisations were targeted by APT41 actors in 2019. Further, it claims four additional telecoms entities were targeted by separate threat groups with suspected Chinese state-sponsored associations.
“The use of MESSAGETAP and targeting of sensitive text messages and call detail records at scale is representative of the evolving nature of Chinese cyber-espionage campaigns,” a FireEye statement said.
“Beyond telecommunication organisations, other client verticals that possess sensitive records related to specific individuals of interest, such as major travel services and healthcare providers, were also targeted by APT 41.
“This is reflective of an evolving Chinese targeting trend focused on both upstream data and targeted surveillance,” it added.



